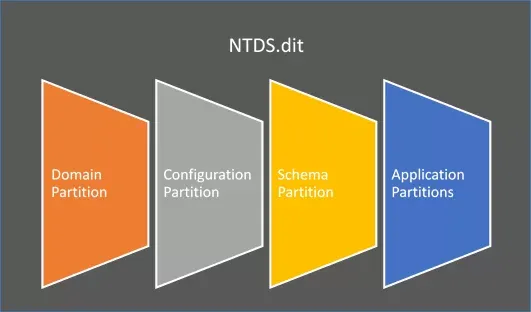
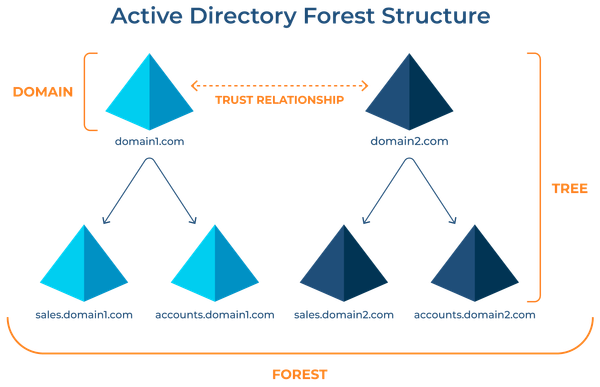
Analyzing Modern Hybrid Identity: Active Directory, Azure, and Entra ID Integration
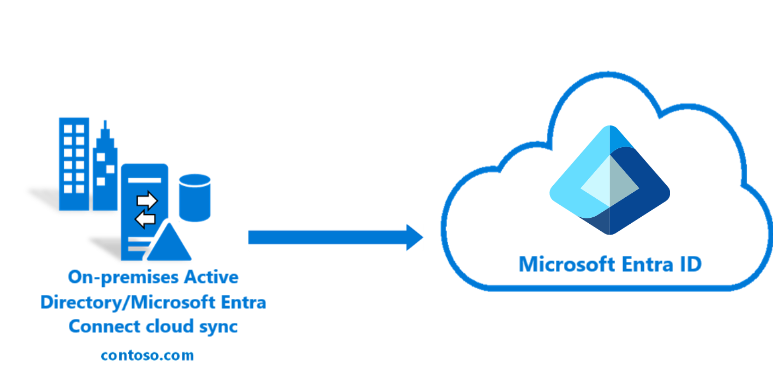
Imagine a bustling global company, “Contoso Ltd.,” at the crossroads of tradition and innovation. For years, Contoso’s IT backbone was its on-premises infrastructure—servers humming in climate-controlled rooms, domain controllers managing access, and employees tethered to their desks. But as the world shifted—remote work surged, cloud apps proliferated, and cyber threats evolved—Contoso faced a new challenge: How could it blend its trusted legacy systems with the agility and scale of the cloud, without compromising security or user experience?
The answer lay in hybrid identity, a seamless integration of on-premises Active Directory (AD) with cloud services like Azure and Microsoft Entra ID. Let’s walk through this transformation, using the architecture diagram as our map.
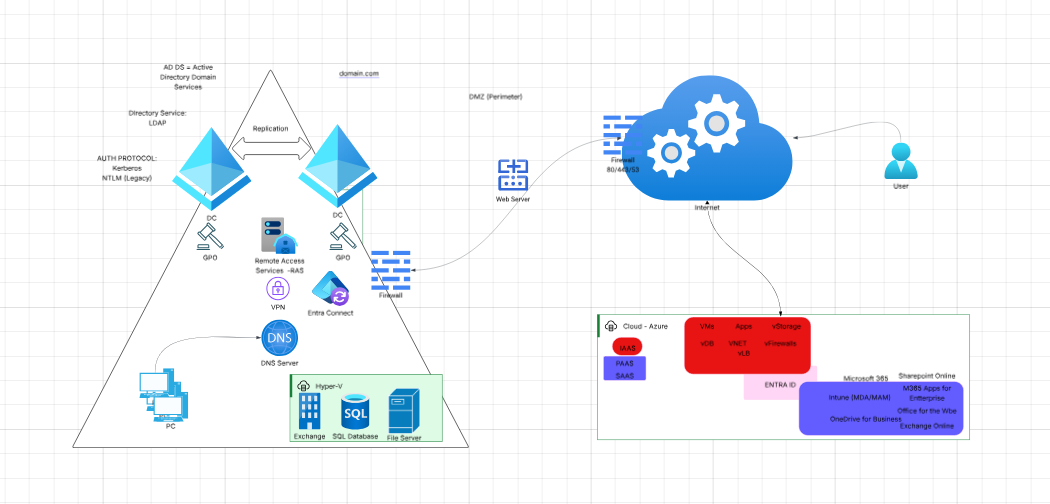
Imagine a bustling global company, “Contoso Ltd.,” at the crossroads of tradition and innovation. For years, Contoso’s IT backbone was its on-premises infrastructure—servers humming in climate-controlled rooms, domain controllers managing access, and employees tethered to their desks. But as the world shifted—remote work surged, cloud apps proliferated, and cyber threats evolved—Contoso faced a new challenge: How could it blend its trusted legacy systems with the agility and scale of the cloud, without compromising security or user experience?
The answer lay in hybrid identity, a seamless integration of on-premises Active Directory (AD) with cloud services like Azure and Microsoft Entra ID. Let’s walk through this transformation, using a modern architecture as our map.
The Foundation: On-Premises Active Directory
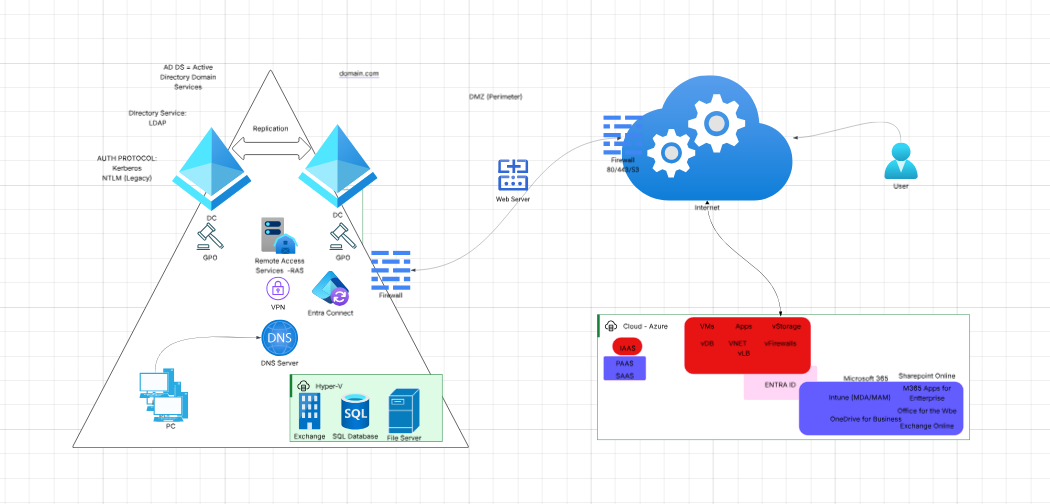
At the heart of Contoso’s legacy infrastructure sits the Active Directory Domain Services (AD DS). Here, domain controllers (DCs) enforce security policies, manage user authentication, and orchestrate access to resources using protocols like Kerberos and NTLM. The DNS Server ensures that every device—from PCs to file servers—knows where to find what it needs.
Critical business applications—like Exchange for email, SQL databases for data, and file servers for documents—often remain on-premises for compliance, performance, or business continuity reasons.
Crossing the Bridge: Hybrid Integration
Contoso’s world is expanding. Employees want to work from anywhere. Customers expect instant, secure access. Enter the hybrid integration layer:
- Remote Access & VPN: Employees connect securely from home or on the road.
- Firewalls & DMZ: Act as sentinels, protecting internal networks while allowing safe communication with the outside world.
- Web Server (Perimeter): Hosts applications accessible to partners and clients, bridging internal and cloud environments.
The real magic happens with Entra Connect (formerly Azure AD Connect). This tool synchronizes user identities, passwords, and groups between on-premises AD and Microsoft Entra ID. Now, whether an employee logs in at headquarters or from a beach in Bali, they’re recognized as the same person, with the same permissions.
Embracing the Cloud: Azure and Entra ID
In the cloud, Contoso discovers new possibilities:
- Microsoft Entra ID: The modern identity platform, enabling secure access to cloud apps and services. It supports advanced protocols (SAML, OAuth, OpenID), conditional access, and multi-factor authentication.
- Azure Resources: Virtual machines, storage, and apps are spun up on demand, scaling with the business.
- Microsoft 365 & SaaS: Tools like SharePoint Online, Exchange Online, OneDrive for Business, and Intune empower collaboration and device management, no matter where users are.
Unified identity is the cornerstone. Employees use a single sign-on (SSO) experience, authenticating once to access both legacy and modern resources.
How Hybrid Identity Works: Protocols, Ports, and Authentication
Hybrid identity solutions blend traditional on-premises AD with cloud services like Azure and Entra ID. Here’s a detailed look at how these systems communicate, the ports they use, and when different authentication protocols—such as Kerberos and SAML—come into play.
Core Services Communication: Ports and Protocols
| Service/Protocol | Port(s) | Description |
|---|---|---|
| DNS | 53 (TCP/UDP) | Resolves domain names for internal network communication |
| LDAP | 389 (TCP/UDP) | Directory queries and authentication (unencrypted) |
| LDAPS | 636 (TCP/UDP) | Secure LDAP queries (encrypted with SSL/TLS) |
| Kerberos | 88 (TCP/UDP) | Default authentication protocol for domain logins and service access |
| Kerberos Password Change | 464 (TCP/UDP) | Used specifically for password changes |
| SMB | 445 (TCP) | File sharing and network browsing |
| RPC Endpoint Mapper | 135 (TCP/UDP) | Remote Procedure Call (RPC) endpoint mapping |
| Dynamic RPC Ports | 49152–65535 | Used for RPC communication between domain controllers and clients (Windows Server 2008+) |
| Global Catalog | 3268 (TCP) | Directory searches across multiple domains (unencrypted) |
| Global Catalog SSL | 3269 (TCP) | Directory searches across multiple domains (encrypted) |
| HTTP/HTTPS | 80/443 (TCP) | Used by web-based services, including ADFS and some management interfaces |
| ADFS (Federation) | 49443 (TCP) | Used for Active Directory Federation Services (ADFS) |
These ports must often be opened on firewalls to enable proper communication between on-premises and cloud components.
Authentication Protocols: Kerberos and SAML
Kerberos: The On-Premises Standard
- Where Used: On-premises AD environments for authenticating users and services.
- How It Works:
- When a user logs into a domain-joined device, the device requests a Ticket Granting Ticket (TGT) from the Domain Controller (DC) using Kerberos.
- The DC verifies the request and issues the TGT, which is cached on the client.
- When the user accesses a service (e.g., file server), the client presents the TGT to the DC to get a Service Ticket for that service.
- The service validates the ticket, granting access without ever transmitting the user’s password in plain text.
- Benefits:
- Secure (no plain-text passwords sent)
- Supports Single Sign-On (SSO) within the domain
- Mutual authentication between client and server
SAML: The Cloud and Federation Standard
- Where Used:
- For cloud-based applications and services, especially when integrating third-party SaaS apps or enabling Single Sign-On (SSO) for external apps via Azure AD/Entra ID.
- SAML is also used when federating identities from on-premises AD to Azure AD or other SAML-compatible identity providers.
- How It Works:
- When a user tries to access a SAML-enabled application, the app redirects the user to the identity provider (Azure AD/Entra ID).
- The identity provider authenticates the user (potentially using Kerberos if the user is on-premises).
- After authentication, the provider issues a SAML assertion (token) back to the application, granting access.
- Benefits:
- Enables SSO across cloud and external applications
- Centralizes authentication and access management
- Works well for integrating with SaaS and third-party services
Real-World Scenarios: Bringing the Diagram to Life
1. The Hybrid Workforce
During the pandemic, Contoso’s offices emptied overnight. Thanks to hybrid identity, employees accessed internal systems via VPN and cloud resources via Entra ID. IT enforced security policies through Group Policy Objects (GPO) for on-prem devices and Intune for remote laptops. Productivity never skipped a beat.
2. Phased Cloud Migration
Contoso’s finance team relied on a legacy SQL database. Rather than a risky “big bang” migration, IT synchronized identities to Entra ID and gradually moved workloads to Azure. As each app transitioned, authentication shifted from AD to Entra ID—users barely noticed, but security and agility soared.
3. Securing Remote Access
A cyberattack targeted Contoso’s VPN. Fortunately, cloud services were protected by Entra ID’s conditional access and Multi-Factor Authentication (MFA). Even if a password was compromised, attackers couldn’t breach critical systems.
4. Modern App Development
Developers launched a new customer portal in Azure. By integrating with Entra ID, they provided secure, SSO-enabled access for both employees and external partners, leveraging the same identity infrastructure as the rest of the business.
Summary Table: Protocols and Usage
| Scenario | Protocol Used | Typical Ports | Description |
|---|---|---|---|
| On-premises domain login | Kerberos | 88 | Fast, secure SSO within the domain |
| Password change in AD | Kerberos | 464 | Secure password change operations |
| Accessing cloud SaaS via Azure AD | SAML | 443 (HTTPS) | SSO and federation for cloud and third-party applications |
| Directory queries (internal) | LDAP/LDAPS | 389/636 | User and device lookup, authentication |
| File sharing | SMB | 445 | Access to shared files and folders |
| Federation (ADFS, Azure AD Connect) | SAML/OAuth | 443, 49443 | Federation and SSO between on-prem and cloud environments |
The Professional Edge: Why Hybrid Identity Matters
- Unified Experience: Employees remember one password, access everything, and IT reduces support calls.
- Centralized Control: Admins manage users and devices from both AD and Entra ID, applying policies consistently.
- Enhanced Security: Modern authentication, conditional access, and MFA protect both cloud and on-prem assets.
- Scalability: Azure resources scale up or down as needed, supporting growth and innovation.
Conclusion: The Road Ahead
Contoso’s journey mirrors that of countless organizations worldwide. Hybrid identity isn’t just a technical upgrade—it’s a strategic enabler, blending the reliability of on-premises systems with the innovation of the cloud. By integrating Active Directory, Azure, and Entra ID, businesses unlock new levels of flexibility, security, and user satisfaction—ready for whatever the future holds.