The Living Forest of Active Directory: Trees, Domain Controllers, and the Art of Domain Connection
Imagine a vast digital forest, where each tree represents a lineage of interconnected domains, and at the heart of every tree stands a vigilant guardian—the Domain Controller. This is the world of Active Directory (AD), a foundational technology that quietly orchestrates authentication, authorization, and resource management for organizations of every size.
The Anatomy of an Active Directory Tree
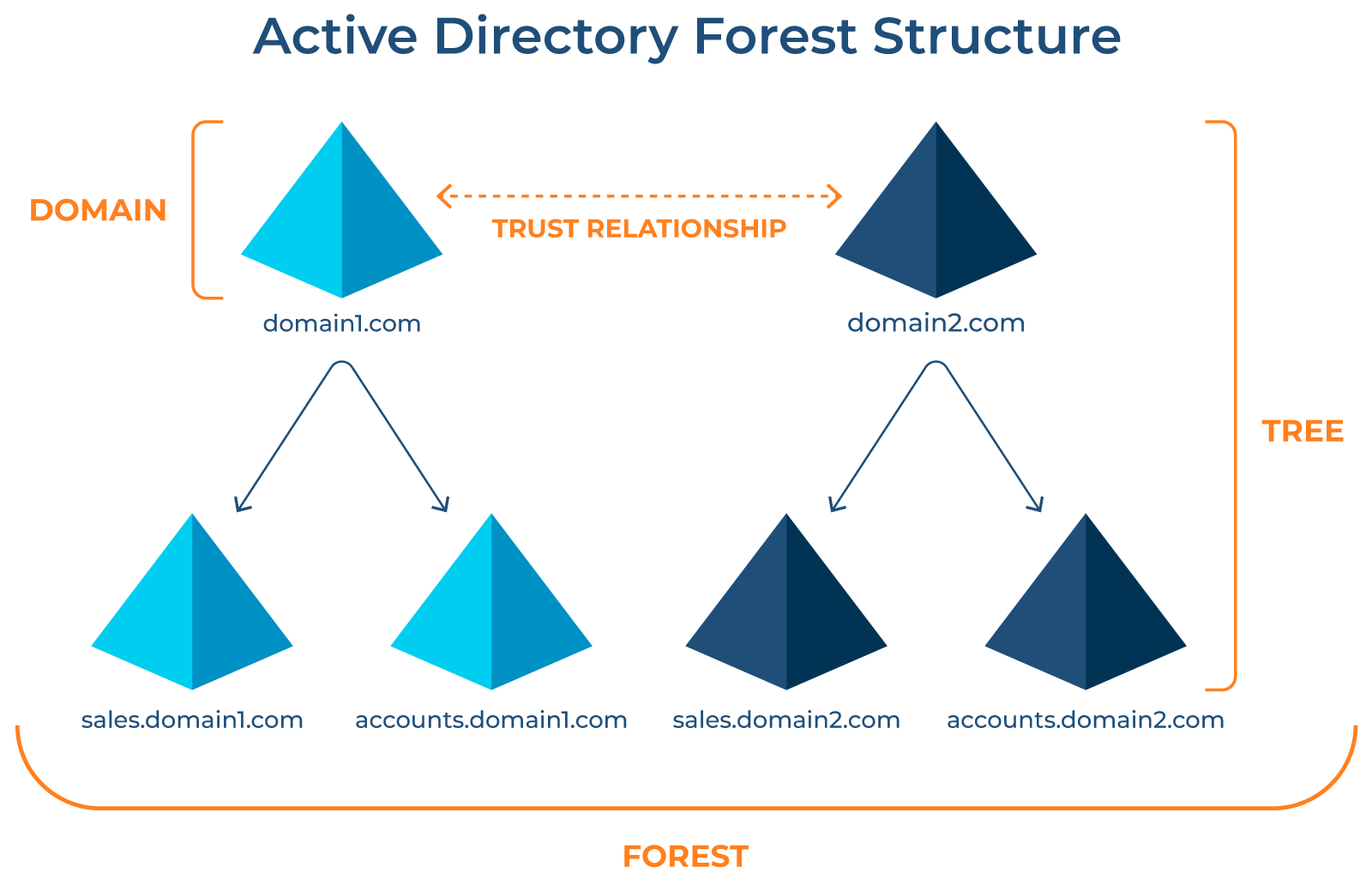
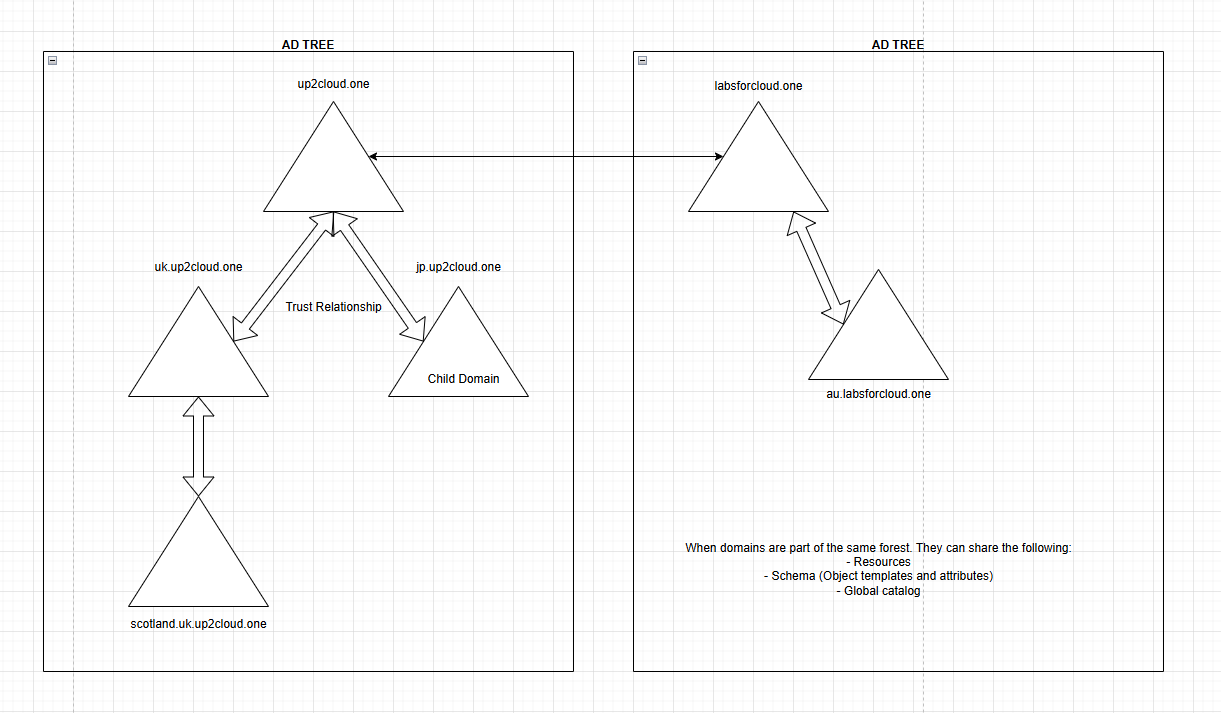
An Active Directory Tree is a hierarchical structure of domains that share a contiguous namespace and a common schema. Think of the tree as a family, with a root domain at the top and child domains branching out beneath it. Each child domain inherits the parent’s name, forming a logical, readable path through the organization’s digital landscape—for example, up2cloud.one as the root, and uk.up2cloud.one or jp.up2cloud.one as children, with further branches like scotland.uk.up2cloud.one.
Key Characteristics
- Contiguous Namespace: All domains in a tree share a single, continuous namespace.
- Transitive Trusts: Trust relationships are established automatically and transitively. If Domain A trusts Domain B, and B trusts C, then A trusts C.
- Shared Schema and Global Catalog: All domains in a tree share the same schema (object templates and attributes) and a global catalog, which acts as a searchable index of objects.
The Role of the Domain Controller
A Domain Controller (DC) is the beating heart of each domain. It’s a specialized server responsible for:
- Authentication: Verifying user credentials and granting access to network resources.
- Authorization: Enforcing permissions and access policies.
- Directory Services: Storing and replicating information about users, computers, and resources.
- Policy Enforcement: Applying group policies across the domain to maintain security and consistency.
Without domain controllers, the forest would be a wild, unmanaged expanse. With them, every login, file access, and resource request is checked and validated, ensuring only the right people get through the gates.
Joining and Merging Domains: When Trees Collide
Organizations evolve. Mergers, acquisitions, or restructuring often require joining or merging domains—sometimes even entire trees or forests.
Joining Domains
- Child Domains: When a new domain is created under an existing one, it becomes a child. The trust is automatic, two-way, and transitive.
- Tree-Root Trusts: When two trees are part of the same forest, a tree-root trust is established, enabling resource sharing and unified authentication.
Merging Domains
Merging domains is a more complex process, often required after company mergers or consolidations. The typical steps include:
- Establish Trust Relationships: Start by creating a two-way trust between the domains.
- DNS Integration: Ensure DNS zones are replicated and resolvable between domains.
- Migration Tools: Use tools like the Active Directory Migration Tool (ADMT) to migrate users, computers, and groups from one domain to another while preserving security identifiers (SIDs) and passwords.
- Testing: Always test the migration in a lab environment before production to minimize risks.
“To merge two domains into one, you can use the Active Directory Migration Tool (ADMT) provided by Microsoft. The ADMT allows you to migrate user accounts, groups, and computers from one domain to another while preserving security identifiers (SIDs) and passwords.”
Trust Relationships: The Glue That Binds
Trust relationships are foundational to how domains and trees interact. There are several types:
Trusts allow users in one domain to access resources in another, subject to permissions and security policies. The transitive nature of most trusts within a tree or forest means that authentication can flow seamlessly, enabling collaboration across an organization’s digital landscape.
The Forest: A Higher Order
A forest is the highest-level container in Active Directory. It can contain multiple trees, each with its own namespace, but all sharing a common schema and global catalog. Forests are often used to provide security boundaries or to accommodate mergers where organizations want to maintain some autonomy while enabling collaboration.
“A forest is a collection of one or more Active Directory domains that share a common logical structure, directory schema (class and attribute definitions), and global catalog.”
Story from the Field: Merging Two Companies
Let’s say Company A (with the up2cloud.one tree) merges with Company B (with the labsforcloud.one tree). Initially, both have their own forest, domain controllers, and policies. To enable collaboration:
- Forest Trusts are established between the two forests.
- DNS Zones are integrated for name resolution.
- Resource Sharing is enabled via permissions and universal groups.
- Over time, the organizations may choose to consolidate into a single forest, migrating users and resources as needed.
Best Practices and Considerations
- Plan Carefully: Merging or restructuring AD environments requires thorough planning and testing.
- Security: Domain controllers are critical assets—protect them with strong security measures.
- Documentation: Keep detailed records of trust relationships, migrations, and changes.
- Testing: Always validate changes in a non-production environment before rolling out.
Conclusion
Active Directory is more than just a technical tool—it’s a living, breathing ecosystem. Trees, domains, and forests form the backbone of secure, scalable, and manageable digital infrastructures. Domain controllers stand as vigilant guardians, while trust relationships weave the fabric that enables collaboration and growth. Whether you’re joining, merging, or simply maintaining your AD environment, understanding these concepts is key to building a resilient and secure organization